Today, as part of our quarterly threat reporting, we’re sharing updates on how our security, integrity and support teams help protect businesses against malware — one of the most prevalent threats across the internet. This includes a behind-the-scenes look at how we tackle this challenge from multiple angles at once: malware analysis and threat disruption, product updates, community support and education, information sharing with other companies and holding threat actors accountable.
Last year, we shared our insights into malicious mobile apps that indiscriminately target the general public and were available in official app stores. Today, we’re publishing detailed findings into aggressive and persistent strains of malware targeting business accounts online.
Because these malicious groups are financially motivated, we expect them to continue probing defenses by diversifying their operations to spread across the internet so they can withstand disruptions by any one company — ours included. That’s why we’re sharing our findings, tips and threat indicators so that the defender community and people using our services can take steps to stay safe.
What We’ve Found
- Our security researchers track and take action against hundreds of threat actors around the world. This year alone, we’ve detected and disrupted nearly ten new malware strains, including those posing as ChatGPT browser extensions and productivity tools, the latest iterations of malware known in the security community as Ducktail, and previously unreported malware families including one we call NodeStealer. Read our technical threat research.
- These malware families target people through email phishing, malicious browser extensions, ads and mobile apps, and various social media platforms with an aim to run unauthorized ads from the compromised business accounts across the internet.
- We’ve identified these malware operations at different stages of their lifecycle and have already seen rapid adversarial adaptation in response to our detection, including some of them choosing to shift their initial targeting elsewhere on the internet.
- As part of our most recent work to protect people and businesses from malicious targeting using ChatGPT as a lure, since March 2023 we’ve blocked and shared with our industry peers more than 1,000 malicious links from being shared across our technologies and reported a number of browser extensions and mobile apps to our peer companies. With each threat investigation, we’ve continued to strengthen how we detect and block these types of malware threats at scale.
- As part of our work against Ducktail malware, we also issued a cease and desist letter to individuals behind it in Vietnam, referred to law enforcement, and will consider all appropriate additional enforcement options against malicious actors behind targeting people on our services.
How Does Business-Targeting Malware Work?
Threat actors go through many stages to target businesses with malware — from developing or acquiring malicious software, to hosting it somewhere online, to spreading and delivering it to targets, and hiding it to evade detection by companies like ours. This complexity makes the threat of business-targeting malware an ecosystem challenge, requiring a concerted effort to combat these malicious operations across our entire industry.
While attack scenarios may vary, threat actors typically disguise malware within innocuous-looking files, as well as mobile apps or browser extensions available in official app stores. Like spammers, they latch onto popular topics like political news or the latest tech or business productivity tools to hide their malware and trick people into clicking on or downloading it.
For example, one of the campaigns we recently disrupted leveraged people’s interest in Open AI’s ChatGPT to lure them into installing malware. In response to detection by our security teams and also our industry peers, we’ve seen bad actors quickly pivot to other themes, including posing as Google Bard, TikTok marketing tools, pirated software and movies, and Windows utilities.
To target businesses, malicious groups often first go after the personal accounts of people who manage or are connected to business pages and advertising accounts. Threat actors may design their malware to target a particular online platform, including building in more sophisticated forms of account compromise than what you’d typically expect from run-of-the-mill malware.
For example, we’ve seen malware families that can attempt to evade two-factor authentication or have the ability to automatically scan for and detect connections between the compromised account and business accounts it might be linked to. See more details in our technical threat research.
Product and Support Updates
To help businesses stay safe across their Meta accounts, we’re continuing to roll out protections against malicious activity:
- New malware removal support: Malware can be designed to re-compromise accounts even after they’ve been recovered by their rightful owners. This leads to a continuous cycle of compromise and recovery that can only be fully resolved when the malware is removed by the user. To help businesses that may have unknowingly self-compromised their devices, we’re launching a new support tool that guides people step-by-step through how to identify and remove malware, including using third-party antivirus tools. Because compromise often occurs outside of our apps and technologies, these stand-alone tools are a critical step in the recovery cycle to help business accounts stay safe.
- Verifying connected Business Manager accounts: We often see threat actors attempt to use compromised accounts to add themselves as business admins to connected business Pages. To help protect against this, we’ve rolled out an ability for businesses to have more visibility and control over administrator changes in Business Manager. For example, businesses can now create restrictions to only allow admins from trusted, selected domains and more effectively audit people’s access through a new active or inactive status filter to assess the status of admins.
- Increasing protections for sensitive account actions: We are expanding authorization requirements for sensitive business account actions like accessing a credit line or changing business administrators. To complete the change, businesses will be prompted to authenticate with two-factor authentication, email verification or co-worker approval. They can also select a trusted employee that is not an administrator to approve sensitive actions.
- Introducing Meta Work accounts: Later this year, we will begin rolling out Meta Work accounts to allow business users to log in and operate Business Manager without requiring a personal account. This will help keep business accounts more secure in cases when attackers begin with a personal account compromise. We plan to test work accounts with a limited set of advertisers this year and aim to expand availability over time. Once work accounts become available, organizations can manage them on behalf of their employees and have access to administrative features including single sign-on, automated account provisioning and more.
How to Know If Your Device is Affected
If you identify unusual behavior on your device or online accounts, it might be a sign that you may have inadvertently downloaded malware. Here are some telltale signs to look out for:
- Suspicious activity on your online accounts that you did not authorize, including financial charges
- Your device runs significantly slower or is frequently freezing
- New toolbars, icons or tabs appear in your browser that you don’t recognize
- Scammy pop-ups appear in your browser
- Shorter device battery life
What to Do If Your Device is Affected
If you believe you’ve downloaded malicious software, we recommend that you delete it from your device immediately, scan your device with up-to-date antivirus software and follow these instructions to secure your personal and business accounts:
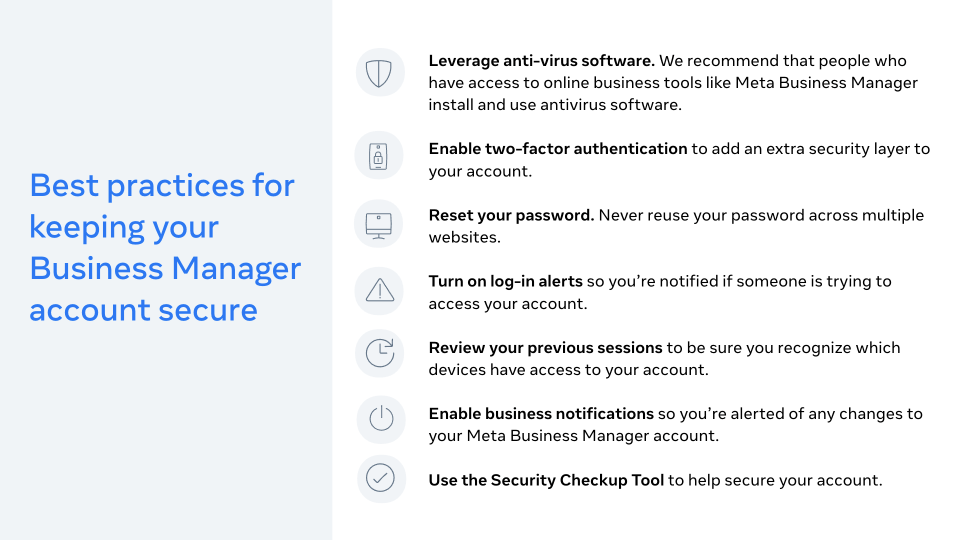
- Leverage anti-virus software: We recommend that people who have access to online business tools like Meta Business Manager install and use antivirus software. Since new malware is created all the time, we encourage you to keep your antivirus tools up to date and enable automatic scanning of files in your antivirus software.
- Enable two-factor authentication to add an extra security layer to your account. Two-factor authentication is one of the most effective tools for combating account compromise attempts.
- Reset your password. Never reuse your password across multiple websites.
- Turn on log-in alerts so you’re notified if someone is trying to access your account, and review your previous sessions to be sure you recognize which devices have access to your account.
- Enable business notifications so you’re alerted of any changes to your Meta Business Manager account.
- Use the Security Checkup Tool to help secure your account.