By Collin Greene, Manager of Product Security
Billions of people use Facebook to connect with the people who matter to them. We have a responsibility to build secure services that help keep people safe.
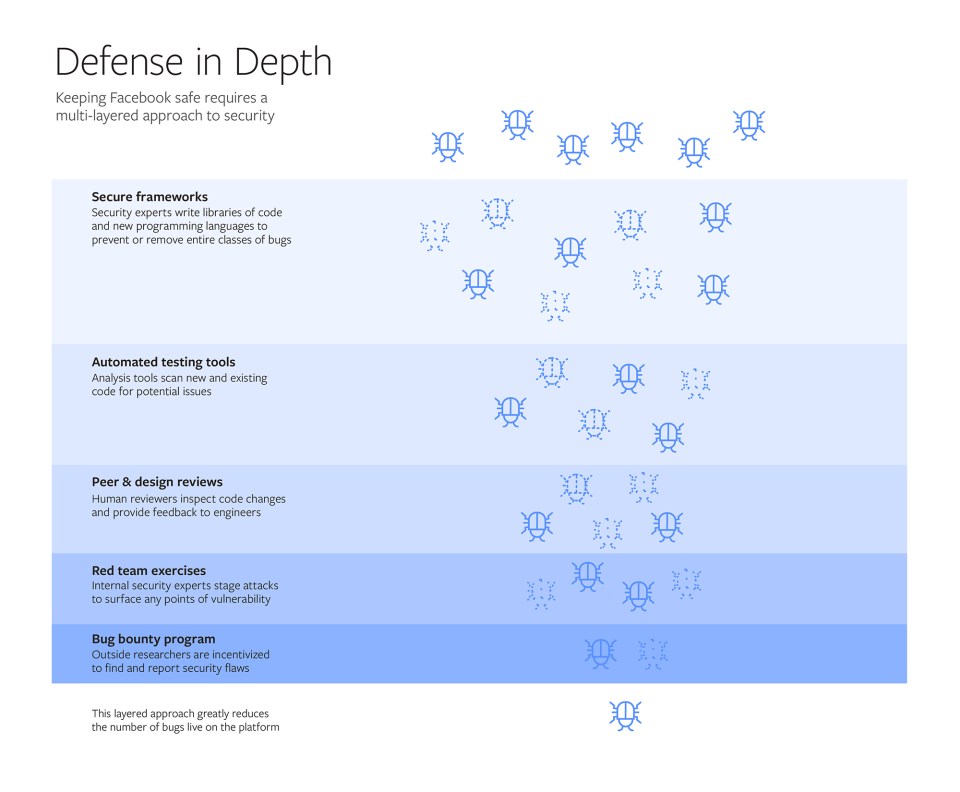
At Facebook we take what’s called a “defense-in-depth” approach to security, meaning we layer a number of protections to make sure we prevent and address vulnerabilities in our code from multiple angles. It is a massive, ongoing effort that spans teams, departments and time zones. Security engineers and practices are embedded throughout the company to help ensure that data protections are built into our code and designs from the get-go, rather than added on at the end.
As it’s practically impossible to write flawless code, it’s not uncommon for software to have bugs. While most bugs don’t have serious consequences, some can create security vulnerabilities that can potentially be exploited to gain access to data or user accounts. Because of this, Facebook is committed to finding, fixing and preventing those bugs. We work to continually improve our defenses so we can counter emerging threats and stay ahead of our adversaries, which means that this type of work is never finished.
In the graphic below, you can see how our “defense-in-depth” approach relies on a combination of technology, expert security teams and the wider security community to help protect our platform. In the following article, we’ll dive into each of these five components — secure frameworks, automated testing tools, peer and design reviews, red team exercises and our bug bounty program — in greater depth.
Secure frameworks: Reduce programming errors
Every engineer who joins Facebook goes through a comprehensive 6-week bootcamp, where they learn the foundational security processes described throughout this post. This ensures that our entire engineering workforce has training in information security.
We also invest heavily in building frameworks that help engineers prevent and remove entire classes of bugs when writing code. Frameworks are development building blocks, such as customized programming languages and libraries of common bits of code, that provide engineers with built-in safeguards as they write code.
One example of a framework we built is called Hack, an update of the popular programming language PHP. Hack helps developers avoid introducing errors by requiring them to explicitly define and type out certain variables and parameters in their code. The addition of this information allows the development software to flag potential errors as the developer is coding. You can think of these requirements like inflatable bumpers in a bowling alley: They channel and guide the actions a programmer can make, in effect limiting the number of errors that may be introduced. As a bonus, the additional information Hack developers must add to their code can make later analysis much easier and helps us develop the analysis tools we’ll describe in the next section. (Coders can read our developer blog post on Hack, which is open source, for more technical details.)
We also created XHP, an open-source augmentation to PHP/Hack that helps engineers integrate PHP and HTML code more seamlessly, reducing the likelihood that errors will inadvertently be introduced into the code. This helps prevent a common type of problem known as a cross-site scripting vulnerability.
Hack and XHP are examples of secure frameworks that help ensure our engineers build technology that is more secure from the very beginning, rather than requiring they write additional code.
Automated testing tools: Analyze code non-stop, automatically and at scale
Since secure frameworks alone can’t anticipate and prevent all issues, we also invest in building analysis tools that can inspect code and find security errors at scale and as quickly as possible.
We are continually learning from security incidents that affect both Facebook and other technology companies, discovering new types of software vulnerabilities and then using this knowledge to prevent similar issues in the future. This is where our preventative and detection-based tools come in.
There are many different types of tools we deploy across Facebook, including static analysis tools, which review written source code, and dynamic analysis tools, which run the code to observe errors as the program is running. These tools look for potential issues so they can either be fixed or flagged for further analysis.
No matter how we find a security bug, we respond by triaging the issue and then doing a root-cause analysis, which allows us to learn from each bug to prevent it — or errors like it — from occurring in the future. This analysis then feeds back into the other phases of our defense-in-depth approach. For example, it may lead to us building new coding frameworks, new tools or new training.
As an example, we built a unique tool that we regularly update to detect new types of bugs. That tool then continually analyzes Facebook’s entire codebase — currently more than 100 million lines of Hack code — to identify these vulnerabilities. It would be incredibly time- and resource-intensive to continually monitor that much code, which changes thousands of times a day, with manual reviewers. This tool allows us to automatically audit our code for certain types of bugs on an ongoing basis.
Peer reviews, design reviews, red team exercises: Use human experts to find flaws technology misses
All code changes go through mandatory peer review in addition to the automated analysis described in the previous section. Certain new features will also undergo design reviews, in which Facebook’s security experts provide feedback to help engineers spot any deficiencies that could lead to security problems. These internal reviews provide another layer of scrutiny to help ensure we are following industry best practices.
To imagine how our products could be misused or attacked, we also run threat modeling exercises, in which we try to anticipate how malicious actors could abuse our systems or misuse our platform. We fix the issues that are surfaced in these exercises and also use these learnings to help design new coding frameworks and analysis tools.
The next layer in our defense-in-depth approach is to regularly test our protections, to verify that our code and our defense mechanisms are behaving as intended and that our response teams are ready and able to detect and investigate attacks. To do that, we have a so-called “red team” of internal security experts who plan and execute staged “attacks” on our systems. These unannounced exercises help provide us a realistic picture of our readiness as we stress-test our systems and processes.
We then take the red team’s findings and, along with other partner teams across the company, map out how we would respond to a similar security incident in what’s known as a “table-top” exercise. This helps us improve the coordination between our teams working on security, privacy, public policy, communications, product and legal and helps us exercise the organizational muscles we would need during a real incident.
Bug bounty program: Engage the global security community
As we face many of the same security challenges as the rest of the technology industry, we have long invested in sharing our tools and knowledge so we can improve our community’s collective defense. In turn, outside information security experts provide their expertise to us through Facebook’s bug bounty program, one of the longest running in the industry.
Since 2011, we have encouraged security researchers to responsibly disclose potential issues so we can fix the bugs, publicly recognize their work and pay them a bounty. Our bug bounty program has been instrumental in helping us quickly detect new bugs, spot trends and engage the best security talent outside of Facebook to help us keep the platform safe. The lessons learned from each report feed back into our larger security effort, making us better and faster at finding, fixing and preventing bugs. To date, we have paid over $7.5 million in bounties to researchers from more than 100 countries. We continue to innovate in this area by expanding the bug bounty program to include issues that can lead to data abuse and compromises of third-party apps on the platform.
A unique mission to protect over 2 billion people on Facebook
Supporting our global community is a great responsibility that has driven continuous improvement and investment in our security technology and talent. Our focus on finding, fixing and preventing security issues has allowed us to scale our defenses as Facebook has grown to support billions of people connecting with one another. At times this has meant adapting our strategies to protect our expanding global community, rewriting our widely-used coding frameworks and open-sourcing unique security tools. And because we know that security work is never 100% finished, our security team will continue to innovate as the Facebook community grows.